Eviction Strategies Tool User Guide
1 Introduction
The Eviction Strategies Tool is an application, developed by CISA, for cybersecurity professionals to use to create countermeasure playbooks based on cybersecurity findings mapped to the MITRE ATT&CK® for Enterprise framework—a knowledge base of cyber threat actor tactics and techniques based on real-world observations.
1.1 Intended Audience
The intended audience for the Eviction Strategies Tool is cybersecurity professionals, such as defensive cyber operations (DCO) engineers, who have familiarity with the MITRE ATT&CK framework.
1.2 What is a Playbook?
A countermeasure playbook is a strategic document that outlines the steps involved in combating a particular threat. For example, Microsoft publishes its own set of pre-built playbooks for responding to threats, such as phishing. The Eviction Strategies Tool allows users to create playbooks that provide countermeasures for one or more ATT&CK techniques.
1.3 What is a Countermeasure?
In the context of the Eviction Strategies Tool, we define a countermeasure as an action or procedure that reduces the vulnerability of an information system to a particular cyber threat actor technique. Therefore, the aim of countermeasures is to eliminate or mitigate the harm that can be caused by such attacks.
1.4 CISA COUN7ER
The CISA COUN7ER project focuses on creating an open source catalog of cybersecurity countermeasures. The Eviction Strategies Tool leverages the COUN7ER dataset as its primary source of countermeasures and includes capabilities that allow for updating to the latest set of countermeasures from COUN7ER's GitHub repository.
- COUN7ER Disclaimer
COUN7ER, including any associated information, playbook, strategies, countermeasures, apparatus, process, product, guidance or any other content, is provided “as is” and for general informational purposes only. Neither CISA nor the United States Government, nor any of their employees, make any warranty, express or implied, or assume any legal liability or responsibility for the accuracy, completeness, suitability, or efficacy of any output or content from COUN7ER. Users hereby acknowledge that using COUN7ER may require expert knowledge and advanced technical capabilities beyond what is typical for members of the public; and that the use or reliance upon the countermeasures, content, or any other information obtained from COUN7ER may cause adverse consequences, including potential device or system failure.
Users assume all risks from the use of COUN7ER, and without limiting the foregoing, users are responsible for any actions they take on systems and devices. In no event shall the United States Government, its employees, or its contractors or subcontractors be liable for any damages including, but not limited to, direct, indirect, special or consequential damages, arising out of, resulting from, or in any way connected with COUN7ER or its use; whether or not based upon warranty, contract, tort, or otherwise; whether or not arising out of negligence; and whether or not injury was sustained from, or arose out of the results of, or reliance upon COUN7ER.
References to any specific entity, commercial product, process, data format or service by trade name, trademark, manufacturer, or otherwise, do not constitute or imply an endorsement, recommendation, or favoring by CISA or the United States Government. All trademarks are the property of their respective owners. Users acknowledge that information within COUN7ER may not constitute the most up-to-date guidance or technical information and COUN7ER is not intended to, and does not constitute advice for compliance, regulatory, or legal purposes. Users should confer with their respective advisors and subject matter experts to obtain advice based on their individual circumstances.
1.5 Contact CISA
Contact CISA Central at 1-844-Say-CISA or Contact@mail.cisa.dhs.gov for questions about the tool.
Visit the CISA Incident Reporting System to securely report cyber incidents to CISA.
1.6 MITRE ATT&CK
The MITRE ATT&CK framework is a knowledge base of cyber threat actor tactics and techniques. The Eviction Strategies Tool uses ATT&CK as a means of defining a standard set of adversarial techniques (e.g., LSASS memory dumping) against which it can build countermeasure playbooks. Cyber threat intelligence (CTI) or other sources such as analyst knowledge may also contribute to playbook techniques. See Best Practices for Mapping to MITRE ATT&CK and https://attack.mitre.org/resources/ for guidance on getting started with ATT&CK.
2 Creating a Playbook
There are three ways to create a playbook using the Eviction Strategies Tool:
- Start a playbook from scratch.
- Create a playbook based on a template.
- Import an existing playbook.
2.1 Starting from Scratch
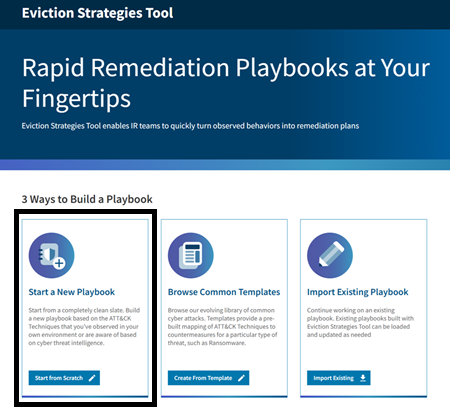
To build a new Playbook from scratch, use the Start from Scratch button on the Eviction Strategies Tool homepage, which creates a new, empty Playbook and navigates to the Add ATT&CK Techniques page, where you can select ATT&CK techniques for the playbook.
2.2 Creating a Playbook Based on a Template

The Eviction Strategies Tool also supports creating playbooks based on templates. Templates, which are pre-built playbooks, center around providing countermeasures against specific types of threats, ranging from malware, such as ransomware, to specific threat actors, like Volt Typhoon. Therefore, templates provide a set of ATT&CK techniques and corresponding countermeasures that can be used on their own as a playbook, or that can be updated with additional techniques and countermeasures.
To create a playbook based on a template, click on the Create From Template button on the Eviction Strategies Tool home page, which will navigate to the Templates page.
2.2.1 Selecting a Template
The Templates page provides a listing of the templates that are currently available in the Eviction Strategies Tool.
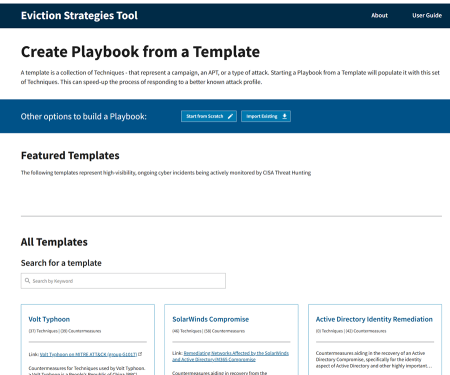
Clicking the More Info... button on a template will open a pop-up that describes the selected template's purpose and provides guidance on how to use it. When exporting a playbook created from a template, this description is included at the start.
Clicking the Select Template button on a template will start a new playbook from that template and opens the Playbook Review page, which allows you to review and delete any unwanted countermeasures.
2.3 Importing an Existing Playbook
Updating and making revisions to playbooks is an important part of their lifecycle. The Eviction Strategies Tool supports this process by allowing you to import previously created playbooks for editing. To import an existing playbook, click on the Import Existing button on the home page, which will bring up an open file dialog that allows you to select a previously exported JSON file.
2.3.1 Import Playbook
After importing an Eviction Strategies Tool JSON file, you will be presented with the Import Playbook page. This page updates, and then displays, the contents of the playbook to be imported.
The playbook update process works as follows:
- Unknown / deprecated Techniques are removed
- Revoked Techniques are replaced
- Unknown Countermeasures are removed
- Outdated Countermeasures are updated to their new versions present in the app
- New Countermeasure mappings for the Techniques are added (*if such Countermeasures were not ignored*)
To finish the import process, click on the Import button.
3 Working With an Open Playbook
3.1 Adding ATT&CK Techniques to a Playbook
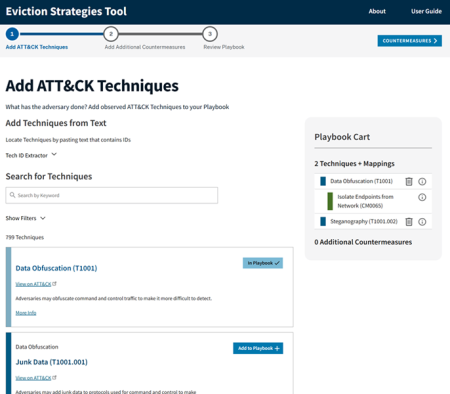
The Add ATT&CK Techniques page allows you to browse and add ATT&CK techniques to your playbook.
The Eviction Strategies Tool incorporates the full set of techniques and sub-techniques from the latest ATT&CK Enterprise release, any of which may be included in a playbook. Future releases of the Eviction Strategies Tool may include techniques and sub-techniques from other ATT&CK domains (for example, Mobile or ICS) if countermeasures mapped to these domains are available.
To help minimize the size of the Add ATT&CK Techniques page, the Eviction Strategies Tool presents ATT&CK techniques as "cards" with just the first line of description text. To view the full details of a technique, including the description, associated tactics, and references, click on the More Info link below the description text on the card to bring up the technique info box.
Both the technique card and the technique info box include a View on ATT&CK link in the top-right corner that navigates to the corresponding technique page on the MITRE ATT&CK website.
Adding a technique to a playbook is simple: Use the Add to Playbook button. To add a sub-technique, either use the Add to Playbook button or select the sub-technique inside of the parent technique's info box and then, similarly, use the Add to Playbook button.
Any techniques or sub-techniques that are added will immediately show up in the Playbook Cart to the right of the techniques list.
3.1.1 Searching for Techniques
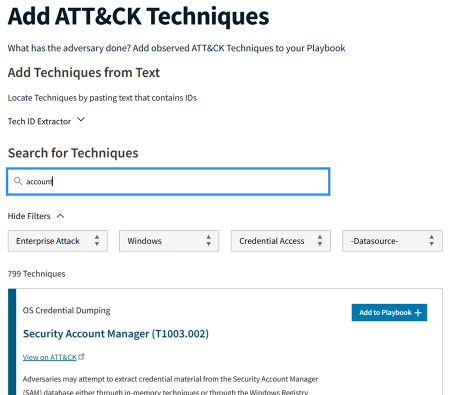
The primary way of finding techniques to add to a playbook is through the search bar. The search bar allows searching by an ATT&CK technique's ID/Name (if known), as well as any key words that may be associated with a technique (e.g., UAC). The returned search results will include any ATT&CK techniques, including sub-techniques, which matched the search query.
3.1.2. Technique Filters
Technique filters allow for refining the set of presented techniques to a smaller, more manageable set.

To use the filters, access the filtering drop-down menu by clicking on Show Filters. The drop-down menu contains four types of filters:
- Domain
- Platform
- Tactic
- Data Source
Filters operate in the following manner with respect to returned results:
- Checking multiple options within a single filter (e.g., Platforms) is a union operation that returns more results.
- Using multiple filters (e.g., Platforms and Data Sources) is an intersection operation on their combined matches and returns fewer results.
You may manually clear individual filters by unchecking filter selections. To clear all filter selections, click on the Clear All Filters button above the filters. To close any of the individual filter selections (e.g., Platforms), simply click outside of the filter.
3.1.2.1 Filter Numbers
The top of each filter includes numbers next to the filter name that indicate:
- In the filter name drop-down buttons: The number of filter options checked / The number of filter options available
- Next to each filter option: The number of results matching this filter option
3.1.2.1.1 How Filter Numbers Update
Checked filter options clear whenever the search text changes. Filter options that match no search results are removed.
The checking/unchecking of options within a filter column will cause the other filter columns to update. Multiple filters represent an intersection and therefore filter each other.
For example: Checking only the Mobile Domain filter option will limit available Platform options to Android and iOS.
3.1.2.2 ATT&CK Domain Filter
The ATT&CK Domain filter (not pictured) is the simplest of the filters available. This filter allows you to select the domains you want to display techniques for.
3.1.2.3 Platforms Filter
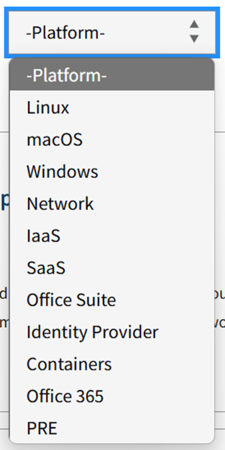
The Platforms filter exposes the set of hardware/software platforms that ATT&CK techniques may be mapped to. Using it, you can filter by the set of platforms utilized within your environment (e.g., Windows only, Windows and MacOS, etc.) to ensure that the returned list of ATT&CK techniques is relevant.
3.1.2.3.1 Note on ICS Techniques and Platforms
ICS techniques do not have directly associated platforms; instead, the assets these techniques target have platforms. Therefore, the Eviction Strategies Tool represents an ICS technique's platform in the filter by listing both the name of the asset that the technique targets and the name of the platform mapped to the asset. This allows easy filtering by names of assets and platforms associated with ICS techniques.
3.1.2.4 Tactics Filter
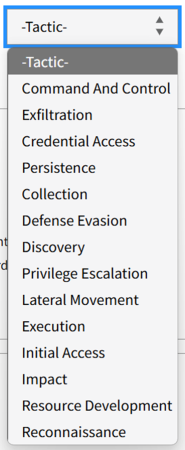
The Tactics filter displays the set of ATT&CK tactics that techniques are mapped to. In ATT&CK, tactics represent the "why" of an ATT&CK technique or sub-technique and the threat actor's tactical goal—the reason for performing an action. Some techniques can be used to achieve multiple goals, and therefore are mapped to multiple tactics.
You use the Tactics filter to select the set of tactics that are relevant to your playbook. For example, to select countermeasures only for techniques that are trying to achieve persistence, select the Persistence value in the Tactics filter.
3.1.2.5 Data Sources Filter
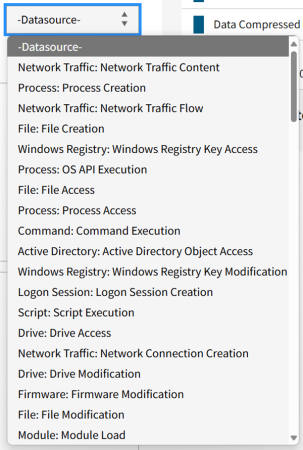
The Data Sources filter displays the set of ATT&CK data sources that techniques are mapped to. In ATT&CK, data sources refer to the types of data that may be collected on a host or network to potentially detect an ATT&CK technique or sub-technique. Therefore, data sources are most relevant to threat hunting and analytics.
For example, you can use the Process Creation data source to detect T1569.002 System Services: Service Execution, by providing the data around newly executed processes that call out to the Windows service control manager. You can therefore filter techniques by data sources that may be available in your environment (e.g., those that are collected by a tool) or are otherwise appropriate for their particular use.
3.1.3 Adding Techniques with the Technique ID Extractor
The Eviction Strategies Tool supports adding techniques extracted from free text through the Technique ID Extractor tool found near the top of the Add Techniques page, under Add Techniques from Text.
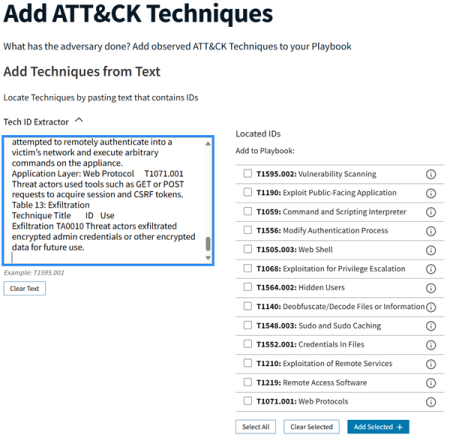
Once opened, the tool presents a text box (under Paste Text Here), in which you can add any free-form text. The tool will extract any ATT&CK technique or sub-technique IDs present in the entered text for possible inclusion in your playbook. Extraction of IDs happens automatically once text is entered into the text box.
Once the available technique or sub-technique IDs have been extracted, the last step in using the Technique ID Extractor tool is selecting the extracted techniques to add to the playbook. To add one or more extracted technique, simply click on the check box to the left of the technique to select it, and then click on the Add Selected button in the bottom right-hand corner.
Similarly, you can select all of the extracted techniques using the Select All button, and you can deselect using the Select None button, both of which are under the list of extracted techniques. As with manually added techniques, any extracted technique that is added will show up in the Playbook Cart, and those that have already been added (and are in the cart) will be listed as such in the Technique ID Extractor.
3.1.4 Cart Overview
The Eviction Strategies Tool Playbook Cart functions much like a traditional e-commerce shopping cart and provides a summary of the selected playbook techniques and countermeasures.
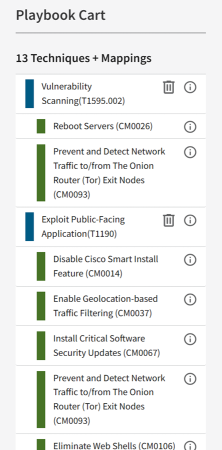
There are two ways to interact with cart items:
- Clicking on the information icon will bring up an info box that contains the full details of a particular technique or countermeasure; the same can be achieved by clicking on More Info when viewing a technique or countermeasure.
- Clicking on the trash can icon will delete an item from the cart.
3.1.4.1 Baseline Countermeasures
By default, the Eviction Strategies Tool includes several "baseline" countermeasures in each custom playbook in the Additional Countermeasure section of the cart. Baseline countermeasures are those that are useful in many scenarios; however, they can be manually deleted by clicking on the trash can icon next to each item.
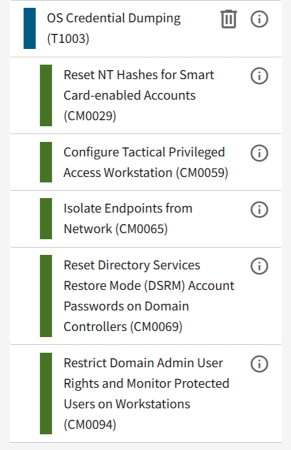
3.2 Adding Countermeasures to a Playbook
The process of adding countermeasures in the Eviction Strategies Tool is largely automated because the tool automatically adds the countermeasures that are applicable for a particular ATT&CK technique once that technique has been added to a playbook. For example, the following countermeasures are automatically added for T1003: OS Credential Dumping:
3.2.1 Additional Countermeasures
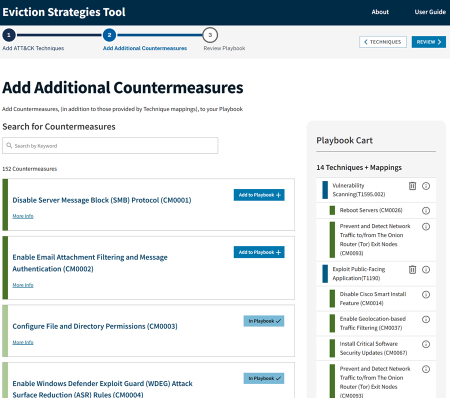
The Eviction Strategies Tool also supports the manual addition of countermeasures, outside of those mapped to ATT&CK techniques. You can access the Additional Countermeasures page, which supports the manual addition of countermeasures, by clicking on the **> Countermeasures** button on the top-right corner of the cart while on the Techniques page. The countermeasures page also allows you to explore the set of countermeasures that are available in the Eviction Strategies Tool.
The interface for the Countermeasures page is very similar to the Techniques page interface except there are no individual filters for countermeasures and the free-text search bar is the only search interface. Any free-form text can be used to find additional countermeasures. Any matching text for the free-text search is displayed in the Matches section at the bottom of each countermeasure.
To view the full text of a countermeasure, click on the More Info button in the bottom left corner of each displayed countermeasure, which will bring up an info box with the information. Once in the cart, clicking on the information icon next to each respective countermeasure will bring up the same info box.
After adding any additional countermeasures, the remaining steps in building a playbook with the Eviction Strategies Tool are reviewing and exporting.
3.3 Reviewing Added Techniques and Countermeasures
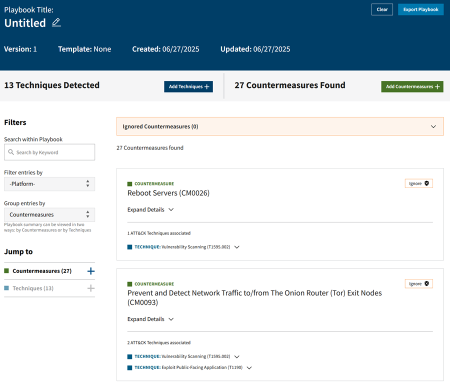
The Playbook Review page provides an overview of the techniques and countermeasures that have been added to the playbook.
You can browse the contents of the playbook using the left-hand navigation menu, which provides a summary of the countermeasures and techniques in the playbook.
COUN7ER countermeasures include mappings to the techniques that they mitigate. As such, playbook entries can be viewed in two different ways on the review page:
- Group by Countermeasures (default): Mitigated techniques appear under each countermeasure. Techniques can be displayed multiple times in this view—once per each countermeasure that is mapped to the technique.
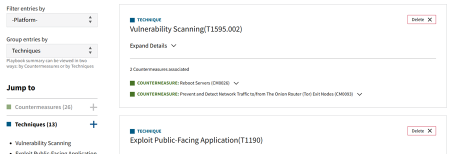
- Group by Techniques: Corresponding countermeasures appear under each technique. Countermeasures can be displayed multiple times in this view—once per each technique that is mapped to the countermeasure.
In addition, the review page includes a search bar that allows searching through entries by keywords, such as countermeasure name or technique ID. Similarly, there is a platform filter that allows for filtering by Windows, macOS, and Linux so that only the countermeasures applicable to the selected operating system(s) are displayed.
3.3.1 Deleting Techniques
In the Group by Techniques view, you can delete techniques from the playbook. Deleting a technique removes it and its mapped countermeasures from the playbook.
3.3.2 Ignoring Countermeasures
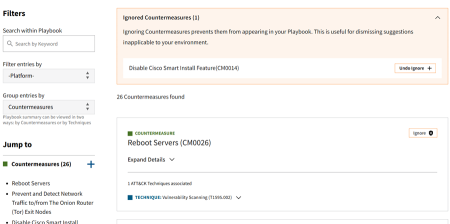
In the default Group by Countermeasures view, countermeasures can be ignored by using the Ignore button. Ignoring a countermeasure will:
- Remove it from every technique it is mapped under.
- Remove it from the Additional Countermeasures section.
- Prevent it from being added as a mapping when adding new techniques.
Using the Ignore button also prevents the countermeasure from being added during updates to an imported playbook. Ignoring certain countermeasures can be useful to ensure that the ones included in a playbook are applicable to your environment.
3.3.3 Deleting Additional Countermeasures
In the Group by Techniques view, you can delete additional countermeasures from the playbook. This only affects the Additional Countermeasures section itself, as techniques will keep their mapped countermeasures.
4. Exporting and Closing a Playbook
4.1 Exporting a Playbook
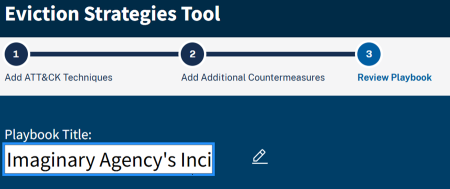
Once the review of a playbook is complete, the final step is to export it in the desired format. Before exporting, change the playbook title from its default value of "Untitled." Changing the playbook title will make the exported playbook files easier to identify, as the title is always included in the exported filenames. To edit the playbook title, click on the edit icon (a pencil and paper) immediately to the right of the current title ("Untitled" by default).
To see the available export options, click on the Export Playbook button at the top right of the page.
4.2 Clearing a Playbook
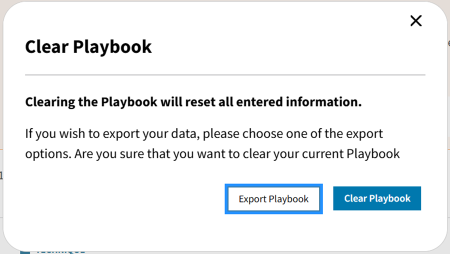
Starting over on the creation of a playbook or importing a different playbook requires clearing the currently open playbook. To do so, on the review page, click on the Clear Playbook button under the Created and Updated timestamps.
Clearing a playbook without first exporting it to JSON will irreversibly destroy your progress. Therefore, clicking on the Clear Playbook button will open an info box for confirming the clear operation.




