Cybersecurity Performance Goals: Assessing How CPGs Help Organizations Reduce Cyber Risk
In October 2022, CISA released the Cybersecurity Performance Goals (CPGs) to help organizations of all sizes and at all levels of cyber maturity become confident in their cybersecurity posture and reduce business risk.
Earlier this summer, CISA outlined four CPGs that organizations could implement as first steps towards better cybersecurity. While we continue to urge every organization to incorporate these fundamental cybersecurity practices, we are encouraged to see and share a few positive trends we’ve identified since they were released.
In line with our Cybersecurity Strategic Plan and our focus on measuring risk reduction, CISA is measuring national progress in adoption of CPGs and associated progress in addressing key risks.
Recently, CISA identified positive trends on two CPGs across nearly 3,500 organizations enrolled in our Vulnerability Scanning service before April 1, 2022. The two CPGs are: Mitigating Known Vulnerabilities (CPG Goal 1.E) and No Exploitable Services on the Internet (CPG Goal 2.W). Of note, these CPGs are particularly important in reducing the likelihood of damaging intrusions across for IT and OT networks.
Reduction in the Average Number of KEVs
Prior to the release of CISA CPGs, the reduction trend in the average number of known exploited vulnerabilities (KEVs) was not consistent. Since the release of CISA CPGs, the organizations enrolled in CISA’s vulnerability scanning service consistently decreased the average number of known exploited vulnerabilities (KEVs) on their networks – the reduction average was almost 20–percent.
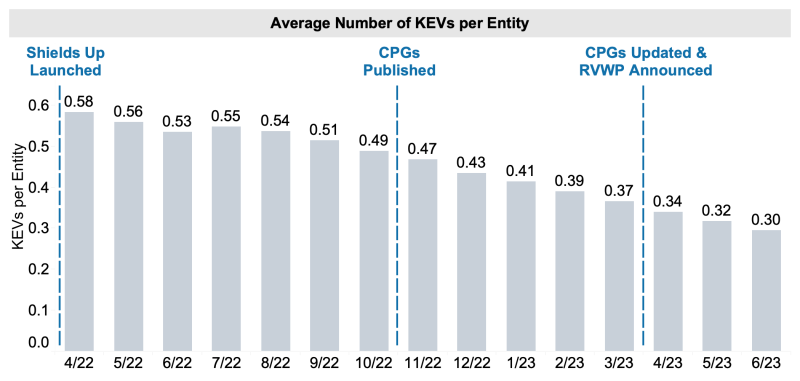
Figure 1: With publication of the CPGs, organizations enrolled in vulnerability scanning continued to demonstrate reductions in KEVs on their networks. |
This decreasing trend shows the progress toward the recommended action of “patching or mitigating
This decreasing trend shows the progress toward the recommended action of “patching or mitigating KEVs on internet-accessible assets” within this CPG.
Progress in Removing Exploitable Internet Services
For organizations enrolled in our vulnerability scanning service, CISA looked for trends in public-facing assets with exploitable services on the internet before CPGs and after CPGs were published. CISA identified that the vast majority of exploitable services exhibited modest declines (1-percent or less) among enrolled organizations.
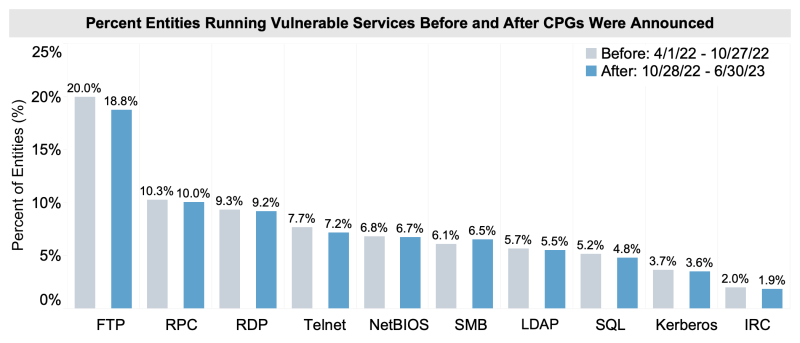
Figure 2: Organizations enrolled in vulnerability scanning demonstrated continued incremental progress in removing exploitable internet services since the CPGs were published. |
Specifically, slight reductions were observed in services such as remote desktop protocol (RDP) and remote procedure call (RPC), which are common attack vectors threat actors use for initial access, ransomware distribution, command and control, and data exfiltration.
Impact of Using Vulnerability Scanning
Organizations enrolled in CISA’s vulnerability scanning continued to show progress with a reduction or maintained an average number of KEVs exposed per entity and gradual reductions in the percentage of entities exposing exploitable internet services. CISA anticipates continued progress toward CPG implementation and risk reduction among organizations enrolled in vulnerability scanning.

Figure 3: Organizations enrolled in vulnerability scanning since the Shields Up initiative started, publication of CPGs, and CPG update and start of Ransomware Vulnerability Warning Pilot (RVWP). |
From April 1, 2022, to June 30, 2023, enrollment in CISA’s vulnerability scanning service increased nearly 69% - more than 5,900 participating organizations.
On average, newly enrolled organizations decreased their vulnerability exposure by 20-percent within the first three months of vulnerability scanning.
Moving Forward
While these trends are progress in the right direction, CISA acknowledges that there is room for improvement - this is only the beginning. Moving forward, we plan to periodically update and expand our analysis of trends that will allow us to track progress and focus our collective efforts on areas that require attention.
CISA also plans to introduce new services and capabilities to simplify CPG utilization and enhance our ability to track national and sector-specific progress.
When an organization uses the CPGs, CISA and our partners can help them understand the specific things they need to do to effectively reduce the specific risks they have identified. Our regional cybersecurity advisors are a valuable resource that can help organizations with assessing their cybersecurity and implementing CPGs.
What You Can Do
Since the CPGs were released, we’ve taken steps to encourage adoption, from the Ransomware Vulnerability Warning Pilot (RVWP) and the Shields Up campaign to our CPG Assessments. These are intended to achieve a simple goal: to encourage adoption of CPGs and reduce the prevalence and impact of cyber intrusions affecting American organizations.
We are taking this journey together and we welcome your contribution. Organizations should consider enrolling (and staying enrolled) in our vulnerability scanning service and conducting a CPG Assessment, a module within our Cyber Security Evaluation Tool (CSET). This assessment can be self-administered or carried out with a regional CISA Cybersecurity Advisor.
If your organization possesses data relevant to CPG adoption, we invite you to let us know about it by reaching out to us at vulnerability@cisa.dhs.gov.
Editor’s note: This blog is not a product of the DHS Office of Homeland Security Statistics or the CISA Statistical Official. Operational data presented in this blog reflect trends identified across organizations enrolled in CISA’s vulnerability scanning service consistent with our commitment to measure and drive risk reduction across our partners.




