ChemLock: Chemical Security on a Budget
Whether a small business or an international company, everyone who interacts with dangerous chemicals has a role to play in understanding the risk and taking collective action to prevent chemicals from being weaponized by terrorists. Below are some simple, effective, and cost-efficient actions to enhance a facility’s security posture.
Security Goals
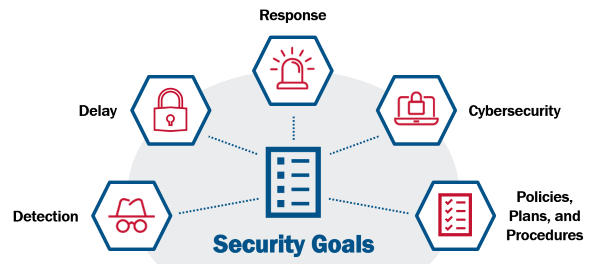
When considering how to optimize chemical security at your facility, it is important to start with an assessment of the different threats and hazards that may affect your facility, the vulnerability of your facility to an attack, and the consequences if the threat were to occur. For example, where are dangerous chemicals located, who has access to them, and how difficult are they to access or remove? Once these risks are assessed, facilities can apply a holistic approach to improve security measures using the five ChemLock security goals.
CISA has security experts across the country that can come to your facility to help you assess and enhance your current security measures.
Learn more about ChemLock On-Site Assessments and Assistance
Detection
- Explore opportunities for low-cost video monitoring systems and alarms.
- Train facility personnel on identifying and reporting suspicious activity.
- Develop an inventory control process to routinely check your chemical holdings, including:
- Maintaining an inventory of quantity and location(s) for each chemical on site.
- Monitoring frequency of access by authorized personnel.
- Identifying the process for tracking receipts and chemical shipments as applicable.
- Ensure adequate lighting to deter and detect intrusion attempts.
The detection security goal includes intrusion detection systems (IDS), camera systems, on-site personnel, lighting, and inventory controls. Learn more about the detection security goal.
Delay
- Consider perimeter and asset barriers that delay intruders and increase time for detection and response.
- Store smaller, portable containers of chemicals in cages or defined rooms with secure doors requiring specific keys, access cards, or keypad codes.
- Consider vehicle identification measures for vehicles to access the premises.
- Ensure access points are locked when not in use or manned.
- Implement an identification check at entry points and a visitor escort policy.
- Implement an access control process to limit restricted-chemical access to appropriate individuals.
- If dangerous chemicals are sold, implement a customer verification process.
The delay security goal includes perimeter and asset barriers, locking mechanisms, access controls, inspections, screenings, and shipping and receiving procedures. Learn more about the delay security goal.
Response
- Initiate and maintain a relationship with local law enforcement and first responders that may be contacted in the event of an incident.
- Consider providing facility points of contact and facility layout information—including locations of dangerous chemicals—to local law enforcement and first responders.
- Develop a crisis management plan considering the multiple threats and hazards that may occur.
- Subscribe to and maintain awareness of National Terrorism Advisory System (NTAS) bulletins and notifications.
The response security goal includes emergency response procedures, crisis management plans, outreach programs, and security plans for elevated threats. Learn more about the response security goal.
Cyber
- Identify all cyber and information systems that monitor and/or control processes that contain dangerous chemicals, manage physical processes that contain a dangerous chemical, or contain business or personal information that, if exploited, could result in the theft, diversion, or sabotage of chemicals.
- Implement password control and password requirements for systems users. Consider:
- Requiring password changes at least once every 60 to 180 days.
- Implementing password protocols to deter easy-to-guess passwords (i.e., 8-character minimum, uppercase and lowercase letters, at least one number and symbol, etc.).
- Refraining from using shared passwords between users on a common device or system.
- Require two-factor authentication to critical systems.
- Install software patches so that attackers cannot take advantage of known problems or vulnerabilities.
- Install firewalls and anti-malware software to protect local operating systems.
- Back up all critical information, store backups offline, and test backups periodically.
- Provide cybersecurity training to personnel.
- Subscribe to CISA Cybersecurity Alerts and Advisories.
Policies, Plans, and Procedures
- Develop and provide procedures regarding access to chemicals and audit them annually to ensure they are up to date. Identify persons responsible for each procedure and ensure they are trained and aware.
- Maintain inventories of key cards, devices, or keys that give access to chemicals.
- Consider implementing background checks on employees with access to dangerous chemicals.
- ChemLock has a personnel background check template that you can customize to meet your specific needs and requirements.
- Conduct a chemical security awareness training for personnel and conduct routine drills and exercises to practice response to facility security incidents.
- ChemLock training courses can help you to ensure that your personnel are trained on the threats and security measures.
- Develop and implement policies for inspecting and maintaining security equipment.
- Develop an incident reporting protocol. Ensure incidents are reported to local authorities and to CISA at central@cisa.gov, as appropriate.
The policies, plans, and procedures security goal includes maintenance, inspection, and testing of security equipment, security awareness and training programs, personnel background checks, and insider threat program, among others. Learn more about the policies, plans, and procedures security goal.
Cybersecurity Resources

Free Cybersecurity Services and Tools
In addition to offering a range of no-cost CISA-provided cybersecurity services, CISA has compiled a list of free services and tools provided by private and public sector organizations across the cyber community.

Cyber Guidance for Small Businesses
CISA offers a different kind of cybersecurity advice for small businesses and their employees. Learn more about how your small business can address cyber threats.

Cybersecurity Best Practices
CISA provides information on cybersecurity best practices to help individuals and organizations implement preventative measures and manage cyber risks.

ChemLock Security Plan
To help facilities use the ChemLock security goals to develop a security plan or evaluate an existing plan, CISA has a guidance document and security plan template that facilities can download and customize for their facility.
ChemLock Services and Tools
From on-site consultations to chemical security training, the CISA ChemLock program offers scalable, tailored options for facilities looking to enhance their chemical security posture.

ChemLock On-Site Assessments and Assistance
CISA's ChemLock program provides on-site assistance and assessments that can help your facility identify the security risks your on-site chemicals present and offer tailored, scalable suggestions for security measures that work best for you.

ChemLock Resources
ChemLock resources are no-cost, publicly available guidance documents, templates, fact sheets, and flyers to help you enhance the cyber and physical security surrounding your chemicals.
ChemLock Exercises
ChemLock Exercises can help facilities test a security plan by either facilitating a live tailored tabletop exercise or providing CISA Tabletop Exercise Packages (CTEPs) that facilities can download and use as needed.

ChemLock Training
CISA offers live, on-demand training to assist owners, operators, and facility personnel with understanding the threats that chemicals pose and what security measures can be put into place to reduce the risk of dangerous chemicals being weaponized.
Contact Information
For more information or questions, please email ChemLock@cisa.dhs.gov.




