Small and Medium Businesses
Small- and medium-sized businesses are key to vibrant communities, a strong economy, and often play critical roles in the supply chain. CISA offers free information and tools to help small businesses protect their people, customers, intellectual property, and other sensitive data cyber and physical threats.
Featured Content

Active Shooter Preparedness
Active shooter incidents are often unpredictable and evolve quickly. Amid the chaos, anyone can play an integral role in mitigating the impacts of an active shooter incident.

Bombing Prevention
Explore resources that protect life and critical infrastructure and build capabilities to prevent, protect against, respond to, and mitigate bombing incidents.

Cross-Sector Cybersecurity Performance Goals
The CPGs are voluntary practices that outline the highest-priority baseline measures businesses and critical infrastructure owners of all sizes can take to protect themselves against cyber threats.

Cyber Guidance for Small Businesses
Cyber incidents have surged among small businesses that often do not have the resources to defend against devastating attacks like ransomware. The security landscape has changed, and our advice needs to evolve with it.

Secure by Design
Every technology provider must take ownership at the executive level to ensure their products are both secure by design and secure by default.

Stop Ransomware
StopRansomware.gov is the U.S. Government's official one-stop location for resources to tackle ransomware more effectively.

The Power of Hello
Industries face a variety of threats, both internal and external, from hostile governments, terrorist groups, disgruntled employees and malicious introducers. Alert employees can spot suspicious activity and report it.

Shields Ready
CISA’s Shields Ready campaign is about making resilience during incidents a reality by taking action before incidents occur.

Small Business Week
CISA proudly celebrates the nation’s entrepreneurs and small businesses and their contributions to the economy during National Small Business Week!

Supply Chain Risk Management Resources
Explore resources developed by the ICT SCRM Task Force that can assist small and medium businesses with their establishment and conduct of supply chain risk management programs and policies.

ChemLock
CISA's ChemLock program is a voluntary program that provides facilities that possess dangerous chemicals with no-cost services and tools to help them better understand the risks they face and improve their chemical security posture in a way that work
Alerts & Directives
Alerts provide timely information about current security issues, vulnerabilities, and exploits.
Threat Actors Chained Vulnerabilities in Ivanti Cloud Service Applications
CISA and Partners Release Call to Action to Close the National Software Understanding Gap
Services
CISA has compiled a list of free tools and services to help small and medium businesses further advance their security capabilities. This living repository includes services provided by CISA, widely used open-source tools, and other free tools and services offered by private and public sector organizations.
Infrastructure Survey Tool (IST)

Cyber Resilience Review (CRR)
Helpful Resources
Use CISA's resources to gain important best practices, knowledge, and skills related to Small and Medium Businesses.
Guidance and Strategies to Protect Network Edge Devices
National Cyber Incident Response Plan Update Public Comment Draft
Enhanced Visibility and Hardening Guidance for Communications Infrastructure
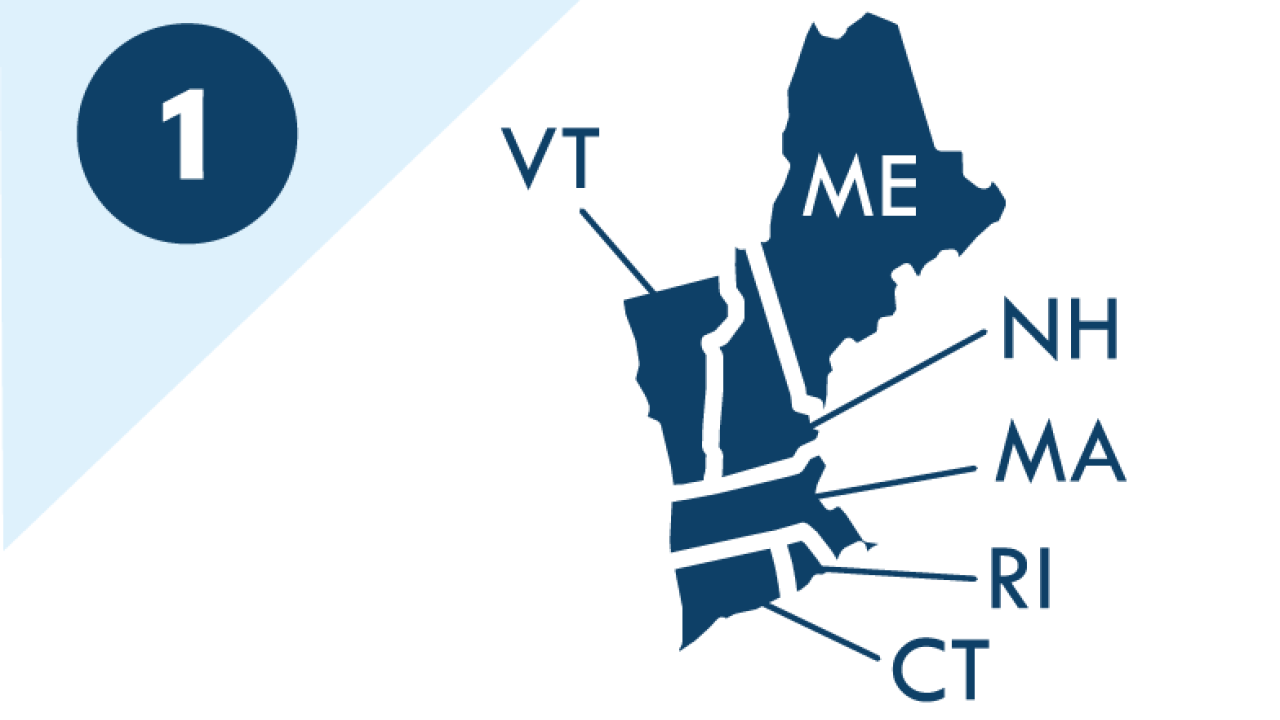
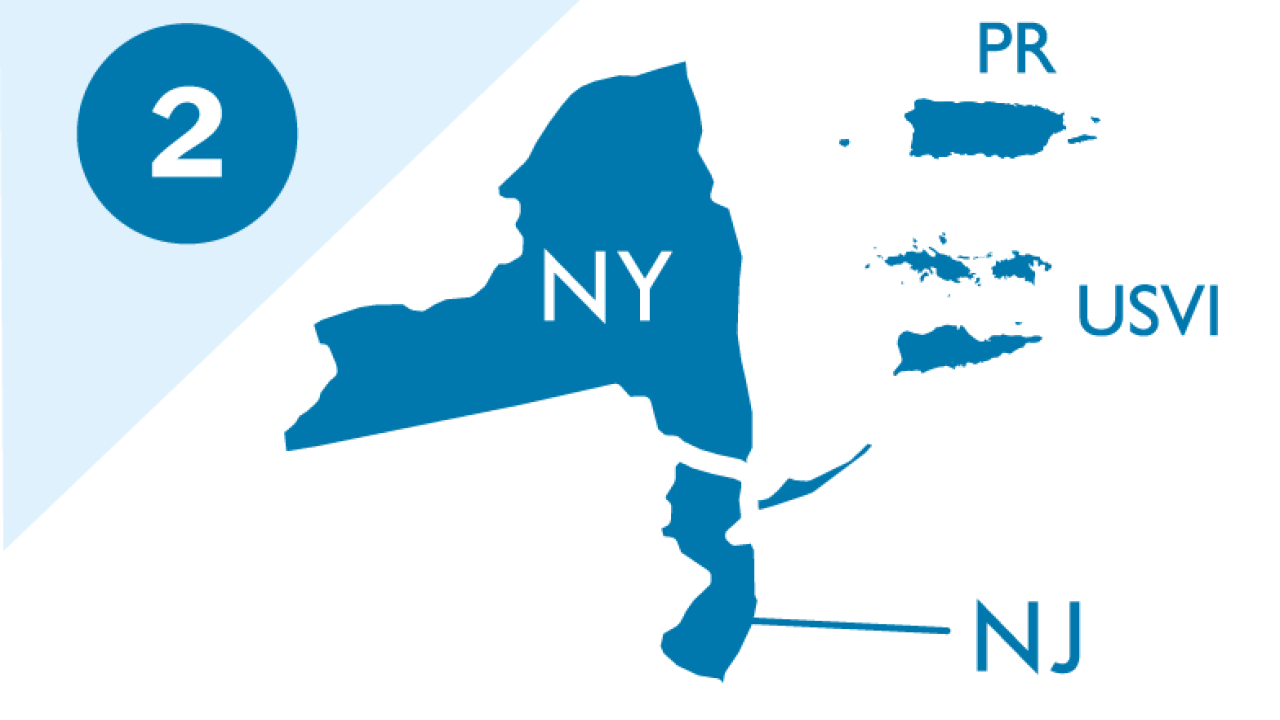
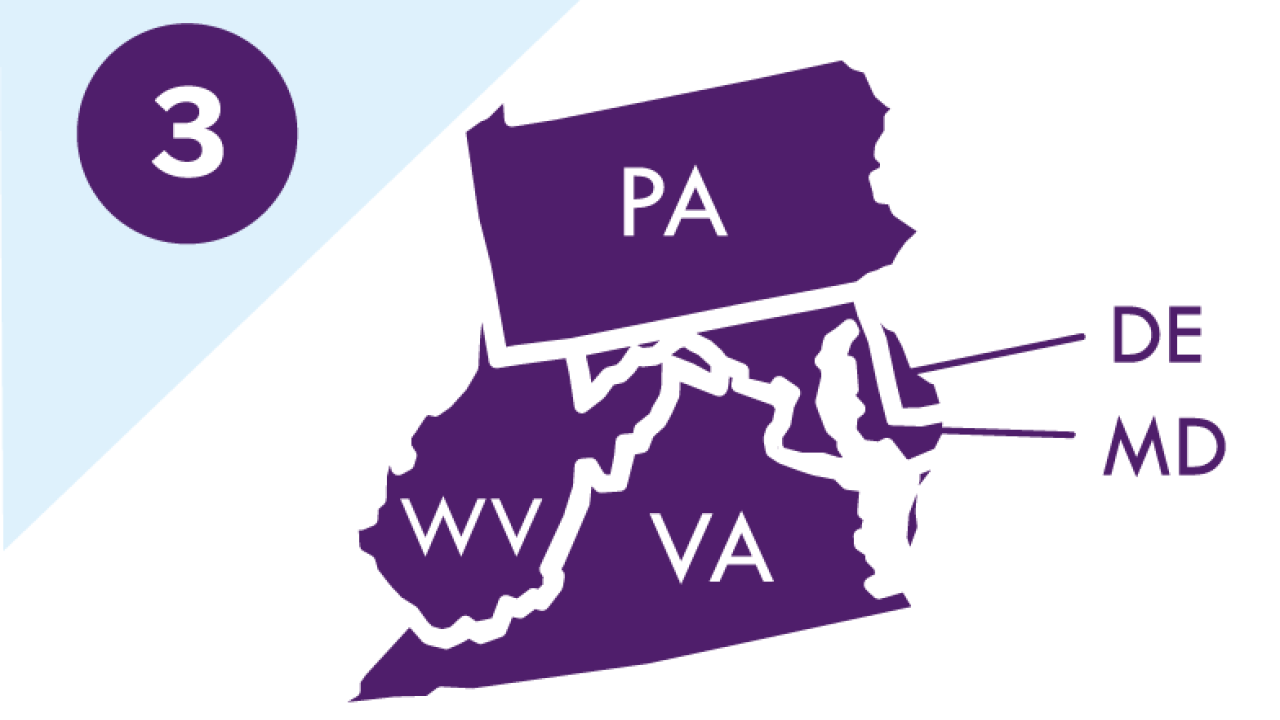
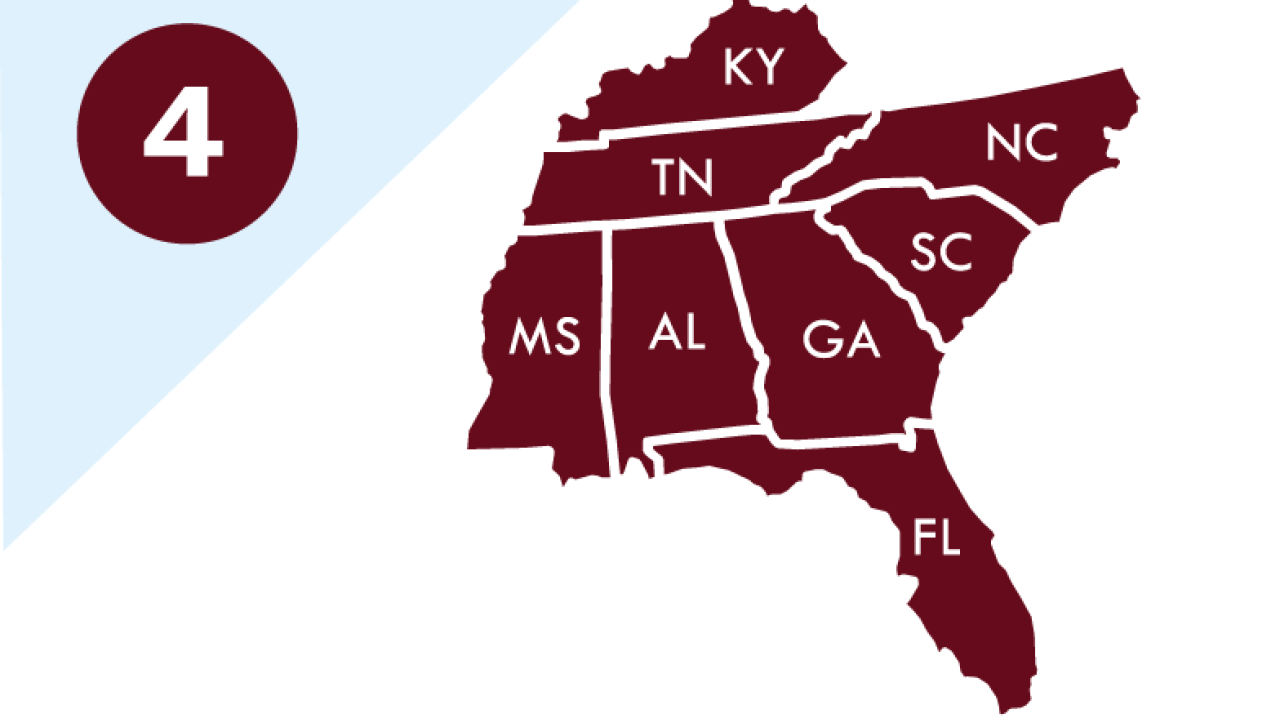
Within each CISA Region are local and regional Protective Security Advisors (PSAs), Cyber Security Advisors (CSAs), Emergency Communications Coordinators (ECCs), and Chemical Security Inspectors (CSIs). These field personnel assess, advise, and assist and provide a variety of risk management and response services to help business, government and other organizations become more resilient to cyber and physical threats and to form partnerships.